Organisations have now accepted remote working as a permanent feature. So, while work from home is becoming a standard, businesses need to rethink and evolve their security models. They need to deploy infrastructure that protects data and monitors how remote workers access resources. And this also applies to partners and third-party vendors that access a company’s system from outside. This article examines the data security aspects and cost benefits introduced by Desktop as a Service (DaaS) solution. A virtual desktop computing environment, enabled by DaaS, is more secure and compliant, backed by support for regulatory standards. It can help to control costs at a granular level.
Let’s begin by comparing two models. In the traditional model, employees use laptops or desktops to access business applications and resources on enterprise networks. And then there is the DaaS model, where users are accessing the same resources stored on a central server, via a web browser on their laptops and desktops.
How Data is protected – a comparison between standalone systems and DaaS
| Standalone desktops and laptops | Desktop as a Service (DaaS) model |
| Applications | Reside on the user’s device | Reside on the centrally located servers |
| Data Risk | Data is lost if the user PC/Laptop is infected by malware or ransomware or due to hardware failure | Data is secured and accessible from any endpoint with a browser |
| Data Theft | Data can be copied by users on USB drives or uploaded to cloud storage | Data is on the cloud; user is only granted access as per his/her privileges |
| Data Backup | IT Admins/Support must physically create backups | Data backup is automated |
| Disaster Mitigation | In case of a data loss, one needs to have the backup restored to continue | Users can access the same work environment and can continue from anywhere as there is no data loss |
Now if the user device is damaged or stolen, or infected by a virus, that would have no impact on the company data, because it is not on the device. The user can use another device (like a tablet or phone or desktop or another laptop) to log in to the virtual desktop environment and continue working. Also, during e-termination of employees, which is prevalent in the current situation, companies are assured that their customer data or any other data as well will not remain with the leaving employee, intentionally or unintentionally.
Don’t you see a clear advantage? Work is not interrupted, and there is no data loss.
Backup, Data Recovery, and Business Continuity
Many businesses are heavily dependent on their data and information systems. As customers transact online or in the physical world, transactional and operational data is moving between the systems. Applications are accessed via mobile phones or laptops. There is a complex interconnection of systems and applications which typically reside on different servers, across data centers, and in multiple clouds. If this data is not available due to data loss or system malfunction, it could disrupt business and result in losses. It would also impact the reputation of the company and affects customer satisfaction. And the same applies to applications – it is imperative to have seamless and uninterrupted access to applications, regardless of which server or cloud they reside.
Data loss/access to data can occur due to various reasons: damaged devices, file corruption, malware infection, or denial of service attacks on servers. An organisation needs to protect its data when it is at rest state, or in motion.
Therefore, it is essential to have robust business continuity and an efficient data recovery plan to mitigate the impact of these disruptions on business operations. This is done through routine backups of servers and clients. In the case of DaaS, the client data is centralised on the server, and hence the backup is done routinely by the server administrator.
What’s more, the entire virtual desktop environment can be replicated to a secondary site in another location. So if there is a natural disaster or a fire at the primary site, operations can switch to the secondary site, and business can continue since the secondary site will have an exact copy (mirror) of the primary site. This model ensures business continuity and data recovery as well.
Virtual desktop service providers can also retain previous versions of the organisation’s data up to 30 days (or more) depending on regulatory and policy requirements of data retention. And this is another reason to opt for DaaS. In the older model (standalone desktops and laptops), everything is done manually, and the onus of doing the backups falls on the organisation and its IT staff.
Compliance
This is a crucial consideration for organisations in regulated industries, like banking and insurance. Today, all industries have strict compliance requirements, because of increased digitisation and the fact that bad actors target all industries. While there are industry-specific regulations and standards for compliance, there are standards (for electronic payments) applicable across all sectors. For instance, HIPAA is a standard for the health insurance industry, but PCI-DSS is a standard requirement of all industries since it relates to electronic payments.
Apart from this, there are standards to certify the infrastructure used by a service provider and pertain to the quality and redundancy of components and data center design and sustainability. An example is the highly regarded industry certifications from the Uptime Institute. Therefore, organisations must do their due diligence and check if the service provider is compliant with all these standards.
Industry certifications for data center providers (such as Uptime Institute) have rigid requirements that ensure they adopt and follow these standards. For instance, Yotta Infrastructure has obtained Tier IV certification by the Uptime Institute. It is also compliant with industry standards such as ISO 27001, ISO 20000, ISO 9000, and PCI-DSS.
Therefore, if your DaaS services are hosted at Yotta’s data center, it complies with all these standards.
Security considerations
The devices used by employees, customers, partners, and vendors to access enterprise apps are known as “endpoint” devices. A Ponemon Institute study reveals that endpoint devices with weak security are a major cause of data breaches. According to the study, 68% of IT security professionals say their company experienced one or more endpoint attacks that compromised data assets or IT infrastructure in 2019, an increase from 54% of respondents in 2017. In the past six years, the global average cost of a data breach has grown by 12%, totaling $3.92 million per breach in 2019, according to the Cost of a Data Breach report by the Michigan-based Ponemon Institute and IBM Security. With regards to India, a report commissioned by IBM revealed that data breaches cost organisations in India about INR 12.8 crore, between July 2018 and April 2019. Human error has a well-documented history of causing data breaches as per research studies, and Spam/Phishing emails are the major cause of data theft.
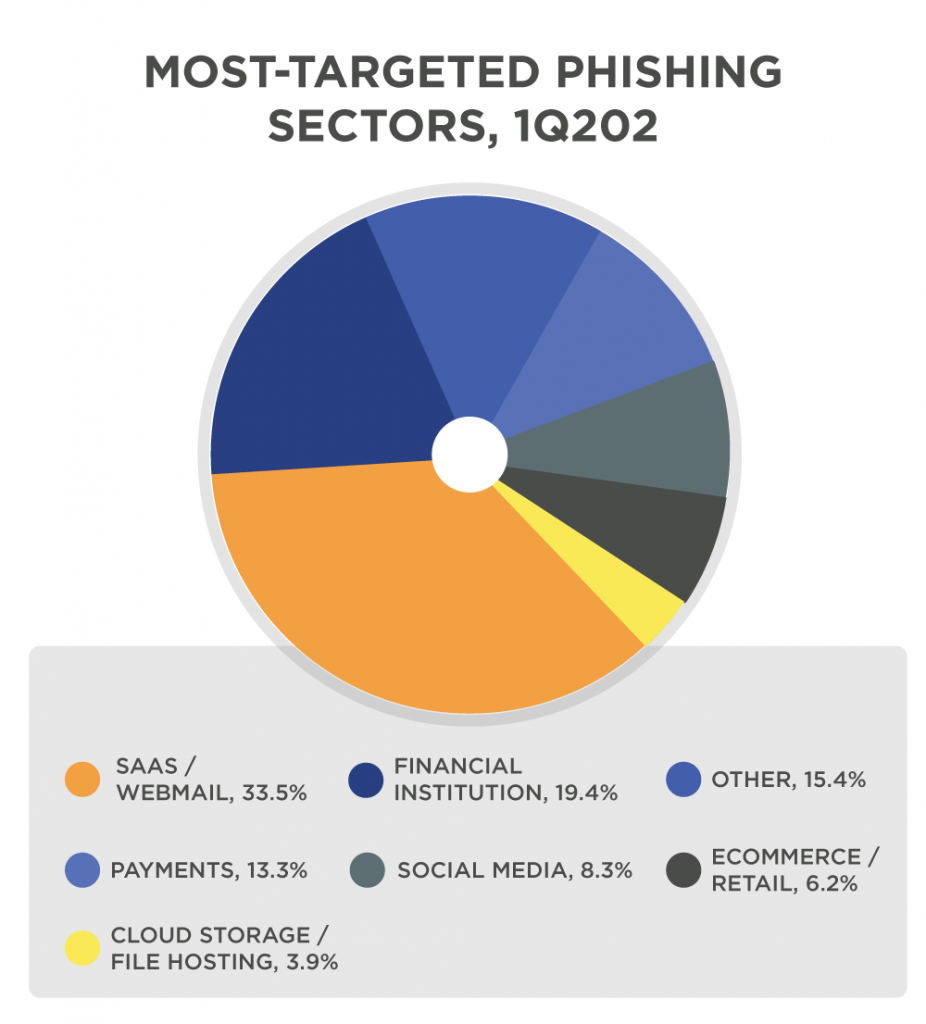
Phishing Activity Trends Report 1stQuarter 2020, apwg.org
The current COVID-19 crisis is also adding to the woes with employees working remotely. Endpoint devices are compromised due to user carelessness and misconfigured software. Users click on links in phishing emails or open malicious email attachments. And this leads them to malicious websites where they unknowingly part with their login credentials. This results in attacks on corporate infrastructure that spread laterally to affect other systems on the network. Breach of user accounts is escalated to privileged accounts that offer additional access to resources. Another reason for endpoint attacks is that users do not update their applications to patch security holes or vulnerabilities.
A DaaS model insulates the enterprise infrastructure from all these attacks. Corporate data is safe even if the endpoint is attacked. That is because this data does not reside on the endpoint.
A trend observed with remote workers today is that they tend to install their collaboration and productivity apps. These apps may be insecure and can compromise enterprise security. But in a DaaS environment, employees can only use company approved applications. And these are pretested and compliant to the organisation’s security policies.
Another security concern is man-in-middle attacks when a bad actor intercepts the client’s communication and the server. It is akin to wiretapping and electronic snooping or eavesdropping. Rest assured this cannot happen when you use a DaaS solution. The endpoint device communicates with the virtual desktop environment on the cloud using a secure tunnel – all communication between the client and the server is encrypted using security standards. Both ends ensure secure communications between the client (browser) and the virtual desktop server. And remember, we are using a browser to access the virtual desktop infrastructure, and today’s browsers support SSL.
So even a man-in-the-middle attack will not lead to a data breach or compromise of user credentials.
Granular Control on Costs
We have seen the various advantages presented by DaaS. But CIOs and business leaders are pressured to cut costs and always do a cost-benefit analysis when evaluating new technologies.
DaaS results in cost savings over the long term, due to humongous savings on software licenses. The savings result from concurrent licensing policies. That means software licenses can be shared among users. And you pay only for as long as you use the application. And you do not have to pay the license fee for the entire suite when you end up using only some applications. For instance, you need not pay to use the whole Microsoft O365 suite – if you need only MS Word and MS Excel, pay only for those applications. Or you can share your AutoCAD licenses among users who work in shifts. This makes for very granular control on costs.
In a virtual desktop environment, your data and infrastructure are secured by the service provider already compliant with industry standards, as discussed earlier in this article. So, the chances of business loss due to ransomware and DoS attacks are minimal.
Conclusion
With businesses adopting distributed models and encouraging remote working, it is essential to ensure the security of these environments. Only DaaS solutions can secure your data and provide a resilient infrastructure that guarantees business continuity and minimal disruption to operations.
DaaS solutions from Yotta Infrastructure are fully compliant to industry standards and ensure the highest security levels for your data and business applications. Yotta delivers DaaS from their Uptime Institute Tier-IV certified data center with highly sustainable Yotta cloud infrastructure.
Finally, the substantial cost savings and granular control on TCO, make DaaS an essential solution for today’s business requirements.

















 Back
Back






